+2349060009680
migration! Optimization! SECURITY!
- DevOps
- Cloud Strategy and Migration
- Cybersecurity Assessment and Monitoring
- Data Protection and Backup Solutions
- Networking
- IT Infrastructure Management
We have secured the trust
12 Years Of Undefeated Success
Partner with Easy Computer Technologies
Join hands with a trusted partner committed to your success. Whether you’re looking to streamline operations, enhance security, or scale your business, we’re here to help you achieve your goals efficiently and securely.
512+
Successfully Project Finished.
12+
Years of experience with proud
1120+
Revenue in 2023 investment
1520+
Colleagues & counting more daily
Take the first step towards a more secure and efficient IT environment
Quality Services
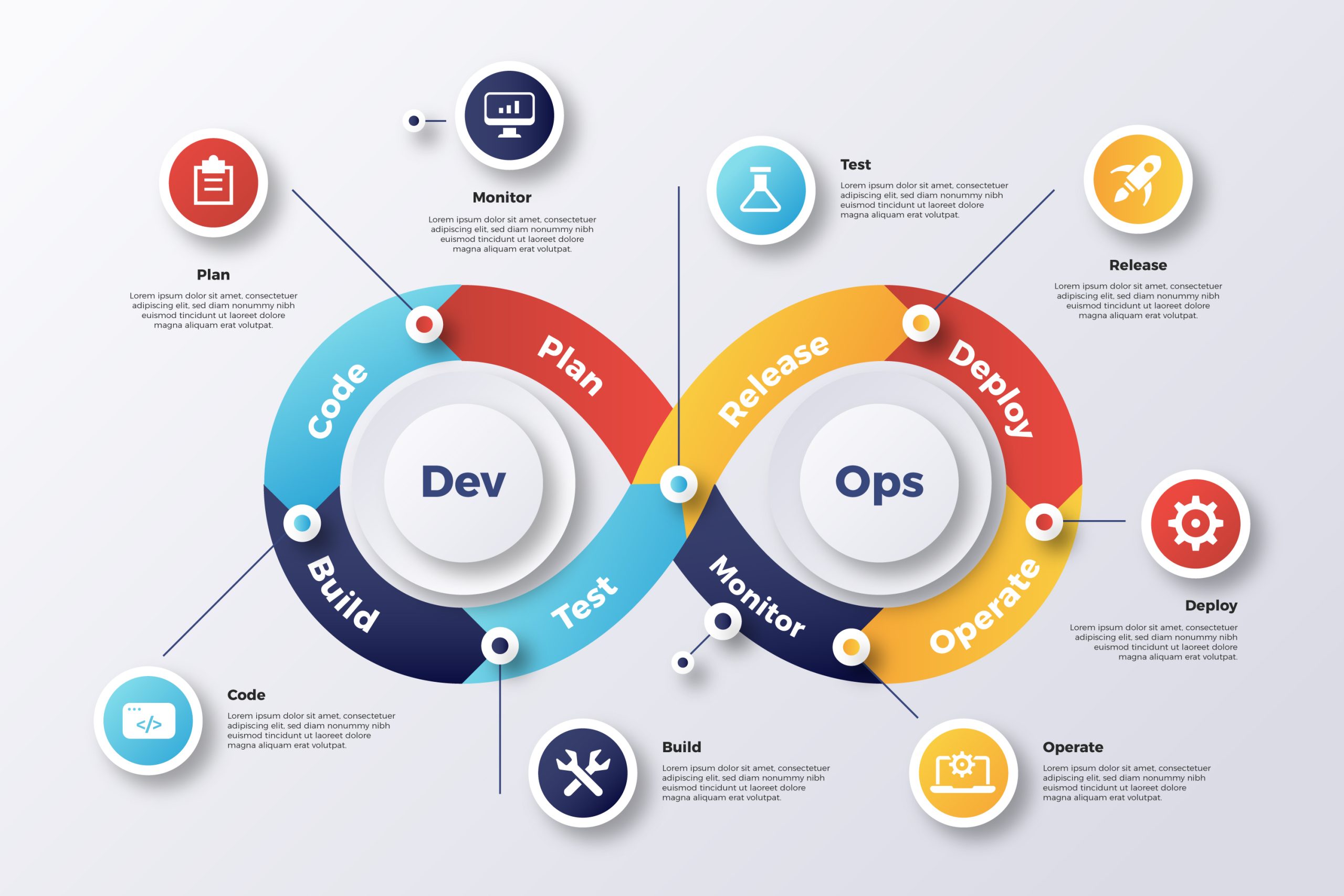
IT and Operations
Automation, Continuous Integration, Continuous Delivery/Deployment, Monitoring and Logging, Collaboration and Communication

We Prevent and Secured
We are proud to be known for the practice of protecting systems, networks, and data from digital attacks

Experience our Networking Infrastructure
Expand your networks over long distances to allow remote offices, branches, or users to access centralized resources and services.

P2P Network
Experience our direct connection established between two nodes or devices, enabling communication exclusively between two endpoints.

AWS! Azure! Hybrid
We provide a broad set of infrastructure services, such as computing power (EC2), storage solutions (S3), databases (RDS), and networking capabilities, among others

Generate sufficient energy
We are leader in sustainable and increasingly affordable solution for generating clean electricity and reducing the environmental impact of energy consumption.
Sustainability
Committed To Innovation
We are prepared to meet your new IT infrastructure, existing and migrating you to cloud or manage your needs using a co-management
We Follow Best Practices
Easy Computer Technologies is one of the leading and fastest growing I.T company across Africa for 12 years, we offer an outright outsourced and annual IT solutions contracts to organizations within the region
- Sustainablility
- Project On Time
- Modern Technology
- Certified Engineers
Sustainability
Transform Your Digital World
we help in minimizing the carbon footprint of IT operations, conserving resources, and promoting a circular economy.
Nigeria
32 Muritala Odofin Plaza, Agungi Bus Stop, Lekki-Epe Expressway. Lagos
We Thoroughly Analyze Your Business Needs Through A Widespread Study Of Our IT SOLUTIONS
We Are Leading International Company In The World
Formalized rules and guidelines
Incident Response
Foster a Culture of Security
Educate employees about security
Effective Policy and Governance
Continuous Improvement
Our Clients Trust Us!
Trust and Worth
What Our Clients Say
Internal Operation Manager
Reuben Amati
Easy Computer Tech prioritizes proactive maintenance, system updates, and access controls, streamlining incident response and enhancing our overall cyber security posture in AGIP.
Cyber Policies and Governance
Folorunsho Reynolds
Easy Computer Technologies cyber security analyst's layered defense approach and continuous learning in Micro World empower us to stay ahead of threats, ensuring a secure IT environment
IT Compliance
Evelyn Adeleke
"Implementing robust cyber security policies and technologies at Triton Intl Corporation has significantly reduced data breaches, ensuring compliance and fostering a security-focused culture. Thanks to ECT.
Snr IT Manager
Barbara Godwins
Easy Computer DevOps Engineers are amazing, the Corporation has drastically improved our deployment speed and collaboration, resulting in higher-quality releases and faster time-to-market.
Request a free site inspection today
Ready To Transform your ICT, Data Security OR Sublet your contracts!
Email us at: info@easycomputertech.com
Learn More From
Frequently Asked Questions
We are leader in implementing DevOps to enhance efficiency and innovation by fostering collaboration, automating workflows, and accelerating software delivery. This leads to faster deployment, improved product quality, and greater responsiveness to market changes and your operations. Our Cybersecurity ensures robust protection against threats, maintaining data integrity, compliance, and trust. It safeguards critical assets, reducing risks and enhancing business continuity. Our Solar energy system adoption significantly cuts energy costs and reduces carbon footprint, contributing to sustainability goals and energy independence. Combined, these practices drive operational excellence, secure and reliable systems, and environmental responsibility, positioning your company as a forward-thinking, resilient, and sustainable organization.
Migrating from onsite servers to the cloud is a significant transition for any organization, involving strategic planning, technical adjustments, and cultural shifts. Here are the key steps we take and the general considerations we suggest for your company:
- Assessment and Planning
- Needs Analysis: We evaluate the current infrastructure, performance, and limitations of your onsite servers. We identify specific needs, such as scalability, disaster recovery, and cost efficiency.
- Cost-Benefit Analysis: We compare the costs of maintaining onsite servers versus cloud services. We consider initial migration costs, ongoing operational costs, and potential savings.
- Cloud Service Selection: We suggest and you choose a cloud provider (e.g., AWS, Google Cloud, Azure) based on factors like services offered, pricing, compliance, and support.
- Designing the Cloud Architecture
- Scalability: We design the architecture to scale up or down based on demand. Leverage cloud features like auto-scaling and load balancing.
- Security: We Implement robust security measures, including data encryption, identity and access management (IAM), and compliance with relevant regulations.
- Redundancy and Reliability: We Ensure high availability and disaster recovery with strategies like multi-region deployments and automated backups.
- Data Migration
- Data Inventory: We Catalog all data to be migrated, prioritizing critical data and applications.
- Data Transfer Methods: We choose appropriate data transfer methods (e.g., online transfer, physical transfer using data transfer appliances).
- Testing: We Perform migration in phases, starting with non-critical data. Conduct thorough testing to ensure data integrity and performance.
- Application Migration
- Rehosting (Lift and Shift): We move applications to the cloud with minimal changes. Suitable for simple applications.
- Replatforming: We make minor adjustments to applications to take advantage of cloud benefits without significant changes to core architecture.
- Refactoring: We redesign and rewrite applications to fully leverage cloud-native features and capabilities.
- Testing and Validation: We test applications in the cloud environment to ensure they work as expected and meet performance requirements.
- Deployment and Integration
- Automation: We use Infrastructure as Code (IaC) tools like Terraform or CloudFormation for consistent and repeatable deployments.
- Continuous Integration and Continuous Deployment (CI/CD): We Set up CI/CD pipelines to automate testing and deployment processes.
- Monitoring and Management: We implement monitoring tools to track performance, usage, and security. And we use management tools for resource allocation and cost management.
- Training and Change Management
- Staff Training: We provide training for your IT staff on cloud technologies, tools, and best practices.
- Change Management: We communicate the benefits and changes to all stakeholders. Address concerns and provide support during the transition.
- Documentation: We maintain comprehensive documentation of the new cloud environment, processes, and procedures.
- Optimization and Continuous Improvement
- Performance Tuning: We continuously monitor and optimize performance. We use cloud-native tools and services for insights and improvements.
- Cost Management: We regularly review and optimize costs. And use tools for cost analysis and budgeting.
- Feedback Loop: We gather feedback from your users and IT staff to identify areas for improvement. And implement updates and enhancements as needed.
The Benefits you get from us when moving to the Cloud
- Scalability: Easily scale resources up or down based on demand.
- Cost Efficiency: Pay-as-you-go pricing models reduce upfront capital expenditure.
- Flexibility: Access to a wide range of services and tools for different needs.
- Disaster Recovery: Improved disaster recovery capabilities with geographically distributed data centers.
- Innovation: Rapid deployment of new features and services to support innovation.
By carefully planning and executing these steps, your organizations can successfully transition from onsite servers to the cloud, leveraging its numerous benefits for enhanced performance, flexibility, and cost efficiency.
We hope this information is sufficient enough for you to make the right decision. Even if you don’t call for our service we will be more than happy to provide you with detailed answer that will enhance your goal.
Implementing cybersecurity in your company involves establishing comprehensive measures to protect sensitive data, systems, and networks from cyber threats. Here’s a brief overview of how you can implement effective cybersecurity:
- Assessment and Planning
- Risk Assessment: we identify and evaluate potential risks and vulnerabilities in your current IT infrastructure.
- Security Policy Development: We develop comprehensive security policies and procedures that align with industry standards and regulatory requirements.
- Implementing Security Measures
- Access Control: We establish strong identity and access management (IAM) policies to ensure that only authorized personnel can access sensitive information.
- Encryption: We use encryption to protect data both in transit and at rest.
- Firewalls and Intrusion Detection Systems (IDS): We implement firewalls and IDS to monitor and control incoming and outgoing network traffic.
- Anti-Malware and Anti-Virus Software: We deploy robust anti-malware and anti-virus solutions to detect and prevent malicious software.
- Network Security
- Segmentation: We divide the network into segments to limit the spread of potential threats.
- Secure Configuration: We ensure that all systems and devices are securely configured and regularly updated.
- Employee Training and Awareness
- Training Programs: We conduct regular cybersecurity training and awareness programs for employees to recognize and respond to potential threats.
- Phishing Simulations: We perform phishing simulations to educate employees about email-based threats.
- Incident Response Planning
- Incident Response Plan: Develop and implement an incident response plan to quickly and effectively respond to security breaches.
- Regular Drills: Conduct regular incident response drills to ensure preparedness.
- Monitoring and Maintenance
- Continuous Monitoring: We use security information and event management (SIEM) tools for continuous monitoring and real-time threat detection.
- Regular Audits: we perform regular security audits and vulnerability assessments to identify and address weaknesses.
- Compliance and Legal Considerations
- Regulatory Compliance: We ensure compliance with relevant regulations and standards (e.g., GDPR, HIPAA, ISO 27001).
- Legal Preparedness: We stay informed about legal requirements and potential liabilities related to cybersecurity.
- Physical Security
- Secure Physical Access: We implement physical security controls to prevent unauthorized access to IT infrastructure and data centers.
- Surveillance and Monitoring: We use surveillance cameras and monitoring systems to detect and deter physical security breaches.
- Vendor and Third-Party Security
- Vendor Risk Management: We assess and manage the security practices of third-party vendors and partners.
- Secure Contracts: We work with you to include cybersecurity requirements in contracts with third parties.
- Continuous Improvement
- Feedback Loop: We continuously gather feedback and learn from past incidents to improve security measures.
- Stay Updated: We keep abreast of the latest cybersecurity trends and threats to adapt and enhance your security posture.
By implementing these steps, a company can establish a robust cybersecurity framework to protect against a wide range of cyber threats and ensure the safety of its digital assets.
Managing IT operations in an organization involves overseeing and coordinating the various activities that ensure the effective and efficient functioning of IT systems and services. Here is a brief overview of how you can manage your IT operations:
1. Strategic Planning
- IT Strategy Alignment: Ensure IT operations align with the organization’s overall business goals and strategies.
- Capacity Planning: Forecast future IT needs and plan for necessary resources and infrastructure to meet those demands.
2. Infrastructure Management
- Hardware and Software Management: Maintain and manage the organization’s IT hardware and software assets, including regular updates and upgrades.
- Network Management: Ensure the reliability, security, and performance of the organization’s network infrastructure.
3. Service Management
- IT Service Management (ITSM): Implement ITSM frameworks like ITIL to standardize service delivery and support processes.
- Help Desk and Support: Establish a help desk to provide technical support and resolve IT-related issues for employees.
4. Performance Monitoring and Optimization
- Monitoring Tools: Use monitoring tools to track the performance of IT systems and applications in real-time.
- Performance Tuning: Regularly optimize systems and applications to improve efficiency and performance.
5. Security and Compliance
- Cybersecurity Measures: Implement robust cybersecurity practices to protect IT assets from threats and vulnerabilities.
- Compliance Management: Ensure IT operations comply with relevant regulations and industry standards (e.g., GDPR, HIPAA).
6. Disaster Recovery and Business Continuity
- Disaster Recovery Plan: Develop and maintain a disaster recovery plan to quickly restore IT services in case of disruptions.
- Business Continuity Planning: Ensure that critical business functions can continue during and after a disaster.
7. Vendor and Asset Management
- Vendor Management: Manage relationships with IT vendors and service providers to ensure reliable and cost-effective service delivery.
- Asset Management: Track and manage IT assets throughout their lifecycle, from procurement to disposal.
8. Budgeting and Cost Management
- IT Budgeting: Prepare and manage the IT budget, ensuring cost-effective use of resources.
- Cost Management: Monitor and control IT operational costs, identifying areas for cost savings and efficiency improvements.
9. Project Management
- Project Planning: Plan and manage IT projects to ensure they are completed on time, within scope, and on budget.
- Agile and DevOps Practices: Incorporate Agile and DevOps methodologies to enhance collaboration and accelerate project delivery.
10. Staff Management and Development
- Team Management: Oversee the IT team, ensuring roles and responsibilities are clearly defined and tasks are effectively delegated.
- Training and Development: Provide ongoing training and professional development opportunities to keep the IT staff’s skills up to date.
11. Continuous Improvement
- Feedback and Metrics: Collect and analyze feedback and performance metrics to identify areas for improvement.
- Innovation and Technology Adoption: Stay informed about emerging technologies and trends to drive innovation and improve IT operations.
By focusing on these key areas, organizations can effectively manage their IT operations to support business objectives, enhance service delivery, and ensure the security and reliability of IT systems and services.
Implementing solar energy in an organization involves several steps to ensure a successful transition to renewable energy. Here’s a brief overview of how to implement solar energy in your organisation:
1. Assessment and Planning
- Energy Audit: We conduct an energy audit to understand current energy usage and identify potential savings from solar energy.
- Feasibility Study: We evaluate the feasibility of solar energy, considering factors such as location, available space (rooftop or ground), and solar radiation levels.
2. Financial Analysis
- Cost-Benefit Analysis: We assess the costs of installation, potential savings on energy bills, and the return on investment (ROI).
- Financing Options: We Explore financing options such as outright purchase, leasing, power purchase agreements (PPAs), and government incentives or grants.
3. System Design and Engineering
- Solar System Design: We design a system that meets your organization’s energy needs. This includes determining the size, type, and configuration of solar panels and inverters.
- Site Assessment: We perform a detailed site assessment to determine the optimal placement and orientation of solar panels for maximum efficiency.
4. Regulatory and Permitting
- Permits and Approvals: We obtain necessary permits and approvals from local authorities and utility companies. This may include building permits, electrical permits, and interconnection agreements.
- Compliance: We ensure compliance with local, state, and federal regulations, as well as industry standards for safety and installation.
5. Installation
- Hiring Contractors: We select experienced and reputable contractors to install the solar energy system.
- Installation Process: We oversee the installation process, which includes mounting the panels, wiring, and connecting to the electrical system. Ensure that the installation follows the design specifications and safety standards.
6. Integration with Existing Systems
- Grid Connection: We connect the solar system to the grid, if applicable, to allow for net metering and potential energy credits.
- Energy Storage: We consider adding battery storage systems to store excess energy for use during non-sunny periods or peak demand times.
7. Monitoring and Maintenance
- Monitoring System: We implement a monitoring system to track the performance and efficiency of the solar energy system in real-time.
- Regular Maintenance: We schedule regular maintenance to clean the panels, check connections, and ensure the system is operating optimally.
8. Training and Awareness
- Staff Training: We train staff on the operation and basic troubleshooting of the solar energy system.
- Awareness Campaign: We promote awareness within the organization about the benefits of solar energy and encourage energy-saving practices.
9. Evaluation and Optimization
- Performance Evaluation: We regularly evaluate the system’s performance against the expected output and savings.
- Optimization: We make necessary adjustments to optimize performance and maximize the benefits of the solar energy system.
Benefits of Implementing Solar Energy
- Cost Savings: We reduce electricity bills and protect against future energy price increases.
- Environmental Impact: We decrease the organization’s carbon footprint and contribute to sustainability goals.
- Energy Independence: We will increase energy independence and reduce reliance on non-renewable energy sources.
- Public Image: We will enhance the organization’s reputation by demonstrating a commitment to renewable energy and environmental responsibility.
By following these steps, your organization can successfully implement solar energy, leading to financial savings, environmental benefits, and improved energy security.
